Once a month I archive my Apache logs. Which involves downloading them from the server and analysing them a little.
This month (last month actually, I am slow with my blogging) there was something obviously unusual from the beginning: instead of the typical six or seven logrotated 50MB access logs I had 15.
While I did hope for a couple of seconds that all of a sudden the popularity of one of my projcts doubled – I suspected immediately that the extra logs were full of bad rather than good things.
And so they were! I opened one of the middle files, access_log.07 and found many many lines like this:
178.65.217.96 – – [24/Mar/2013:04:40:09 -0400] “GET /isomaster/releases/isomaster-1.3w-installer.exe HTTP/1.1” 404 3121 “-” “Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)”
77.35.44.146 – – [24/Mar/2013:04:40:10 -0400] “GET /isomaster/releases/isomaster-1.3w-installer.exe HTTP/1.1” 404 3121 “-” “Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)”
94.51.3.138 – – [24/Mar/2013:04:40:10 -0400] “GET /isomaster/releases/isomaster-1.3w-installer.exe HTTP/1.1” 404 3121 “-” “Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)”
178.65.217.96 – – [24/Mar/2013:04:40:10 -0400] “GET /isomaster/releases/isomaster-1.3w-installer.exe HTTP/1.1” 404 3121 “-” “Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)”
77.35.44.146 – – [24/Mar/2013:04:40:11 -0400] “GET /isomaster/releases/isomaster-1.3w-installer.exe HTTP/1.1” 404 3121 “-” “Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)”
Yep, that’s 3 requests per second. And how long has it been happening? Some quick grep commands found that it started on “21 Mar 08:01:11” and ended on “1 Apr 14:36:26”, that’s 12 days of constant hammering!
The file the requests are for has been removed months ago, I got tired of dealing with the windows version of ISO Master, so my first thought was that this was someone’s broken script that was supposed to download the latest version or something, but then I noticed that the IPs are different. Note that even in the random 5 lines I pasted in above the requests are coming from 3 different IPs!
Sure is starting to smell like a DDOS attack, but why? Who cares enough about my server, or about me to bother wasting valuable botnet nodes on it?
Let’s do some more grep magic, this attack:
- | wc -l: Made a total of 2.6 million requests, that’s 260 thousand requests per day.
- | cut -f 1 -d’ ‘ | sort | uniq | wc -l: Used 1183 unique machines (or at least IP addresses).
- | cut -f 1 -d’ ‘ | sort | uniq -c | sort -b -g | tail -20: Had these 20 worst offenders, check out that last one, two hundred and seventy thousand requests!
24209 46.41.102.187
33104 95.27.161.96
34276 109.201.122.167
35827 178.159.30.31
37249 109.201.103.230
41455 91.124.244.192
41603 176.96.64.243
42493 109.201.119.242
43714 158.46.46.195
47652 95.106.16.222
54098 178.65.217.96
59760 37.229.68.141
67490 188.122.249.84
67596 46.118.177.113
68509 5.142.224.71
107007 178.213.194.220
109235 92.240.209.14
183352 46.185.61.81
197865 109.185.126.177
273314 5.35.29.186
John recently told me that you can use the host command to do reverse DNS lookups, and I did a few, but didn’t record the results, though I remember that 2 out of 3 were russian. Let’s try again now (do you like my mad commandline skills? :))
for IP in `grep ‘/isomaster/releases/isomaster-1.3w-installer.exe’ 2011-mar-access_log | cut -f 1 -d’ ‘ | sort | uniq -c | sort -b -g | tail -20 | sed ‘s/ *//’ | cut -f 2 -d’ ‘`; do host $IP; done
187.102.41.46.in-addr.arpa domain name pointer 187.102.41.46.donpac.ru.
96.161.27.95.in-addr.arpa domain name pointer 95-27-161-96.broadband.corbina.ru.
Host 167.122.201.109.in-addr.arpa. not found: 3(NXDOMAIN)
31.30.159.178.in-addr.arpa domain name pointer peer31-30-159-178.ll.magnitogorsk.multinex.ru.
Host 230.103.201.109.in-addr.arpa. not found: 3(NXDOMAIN)
192.244.124.91.in-addr.arpa domain name pointer 192-244-124-91.pool.ukrtel.net.
Host 243.64.96.176.in-addr.arpa. not found: 3(NXDOMAIN)
Host 242.119.201.109.in-addr.arpa. not found: 3(NXDOMAIN)
Host 195.46.46.158.in-addr.arpa. not found: 3(NXDOMAIN)
Host 222.16.106.95.in-addr.arpa. not found: 3(NXDOMAIN)
96.217.65.178.in-addr.arpa domain name pointer pppoe.178-65-217-96.dynamic.avangarddsl.ru.
141.68.229.37.in-addr.arpa domain name pointer 37-229-68-141-broadband.kyivstar.net.
84.249.122.188.in-addr.arpa domain name pointer 188-122-249-84.clients.tlt.100megabit.ru.
113.177.118.46.in-addr.arpa domain name pointer SOL-FTTB.113.177.118.46.sovam.net.ua.
Host 71.224.142.5.in-addr.arpa. not found: 3(NXDOMAIN)
Host 220.194.213.178.in-addr.arpa. not found: 3(NXDOMAIN)
Host 14.209.240.92.in-addr.arpa. not found: 3(NXDOMAIN)
81.61.185.46.in-addr.arpa domain name pointer 46-185-61-81-sum.broadband.kyivstar.net.
177.126.185.109.in-addr.arpa domain name pointer host-static-109-185-126-177.moldtelecom.md.
Host 186.29.35.5.in-addr.arpa. not found: 3(NXDOMAIN)
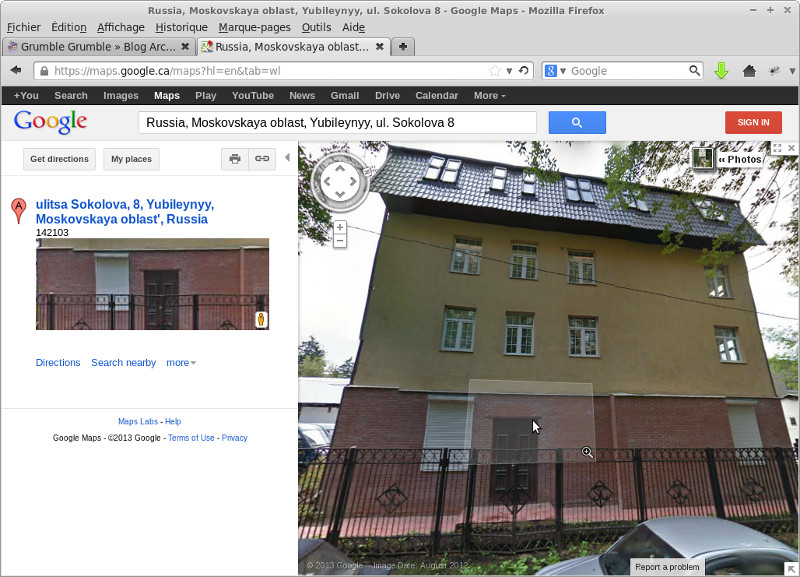
Some of the hosts are no longer online, but pretty much every other one is either from Russia or Ukraine (except the one from Moldova). Interesting. Actually they are not offline, they just don’t have reverse DNS working. The biggest one I found via whois (thank you Gnome Network Tools) has an address and everything:
address: LLC “Multiscan”
address: I.Lukyanova
address: ul. Sokolova, 8
address: 141090 Yubileynyy, Moscow Region
address: RUSSIAN FEDERATION
phone: +74959743623
fax-no: +74957555344
Hm, suspicious looking building, it’s too nice for where it is:
I don’t recall having any enemies back home, in fact I remember eastern europe with fondness. So my guess is this had nothing to do with me (since noone contacted me about it) and is rather some practice or testrun for something or someone or another.
I won’t be able to figure out much more than that (cause I’ll be busy with other things), oh well, it was an interesting experience and I’m quite smug about that my server took it so well that I haven’t even noticed the attack during the 10 days it was going on. And I use this server all day long! Sackware rocks.